See Our Work
About Us
Innovative Knowledge Store Consulting Solutions
The world of artificial intelligence and large language models offer so much promise. We create custom workflows to leverage these capabilities in new and unique ways. Here is an example of how we translate data into insights. Follow this link to see an open source project we helped develop that translates disparate data into insights:
Projects like this are just the start. More interesting and powerful projects are in the work. We seek to transform how data is assembled in a fundamental way!
Our Mission
At Last Heat Technologies, we seek to open the world of possibilities provided by AI advances. It’s not just about refining existing workflows for how you do data and business analytics. It’s about creating entirely new ones!
Our Team

Last Heat is led by Justin Del Vecchio, PhD, who has over 20 years of industry experience. He has worked as a defense contractor and was a senior program manager that led a team of engineers and interns to develop software solutions for government and private industry. Some of these organizations include the Office of Naval Research, IARPA, Army Corps of Engineers, and Army I2WD.
His projects primarily focused upon information fusion of cyber data sources using machine learning algorithms, and the translation of multiple disparate data sources into situational awareness. He became a full time Assistant professor in the Computer Science department at Canisius University in Fall 2022. He happily guides students on learning the software development processes, the art of cybersecurity, and guiding student researchers on the ethical use of large language models.
Our Services
We offer consulting and software engineering services to integrate large language models into your business!
Examples
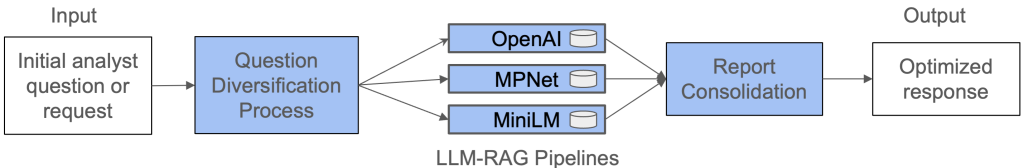
We developed a system to leverage this capability, as shown in the figure above. We used knowledge drawn from the National Security Archive’s timeline of the Ukraine conflict. The system addresses two common questions often asked about LLM-generated content. First, how can the LLM ensure that relevant documents are not overlooked? Second, how can it ensure that the most important documents are included in the response? Here is an example of a question asked of our retrieval augmented generation (RAG) pipeline and some of its response italicized below.
Provide an assessment on the following line of reasoning. The Russians are not using their full set of cyber capabilities in Ukraine as they view it as a training ground. Their cyber attackers are simply honing their skill, pressing the case against the Ukrainians, but show restraint. Provide citations where possible. Find quotes. Also, list out the names of folks who hold these opinions – both in support of this potential fact and against it.”
Mixed Evidence and Strategic Implications
There is also an argument that Russia’s cyber activities are not being fully restrained, but rather, they are part of a more complex strategic approach. Some sources highlight Russia’s careful balancing act—using cyber tactics for strategic gains without triggering an escalatory response from NATO or other Western allies.
Keir Giles, Senior Research Fellow at Chatham House, believes that Russia’s operations in Ukraine have provided an ideal environment for testing cyber tactics in real-world conditions. However, he also notes that Ukraine’s resilience and support from international allies have played a crucial role in limiting the impact of Russian cyberattacks. (Source: Chatham House)
James A. Lewis from CSIS highlights that Russia might be avoiding larger-scale attacks not due to restraint but due to tactical considerations. He suggests that Russia might be preserving its advanced tools for future conflicts while testing their effectiveness in Ukraine. (Source: CSIS – Cyber War and Ukraine)
In line with this, Thomas Rid, a professor at Johns Hopkins University, argues that Russia’s cyber activities in Ukraine are part of a larger strategy of hybrid warfare. Rid emphasizes that the Russian playbook involves integrating cyber operations with other forms of warfare, rather than limiting their scope for training purposes. (Source: Wired Magazine)
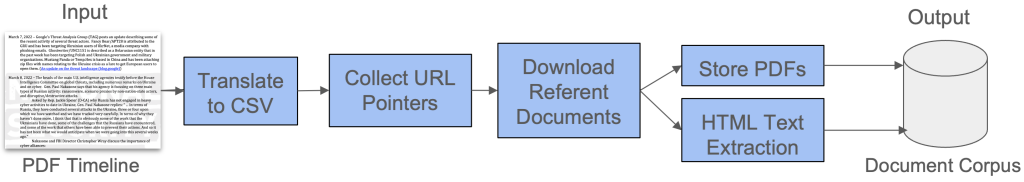
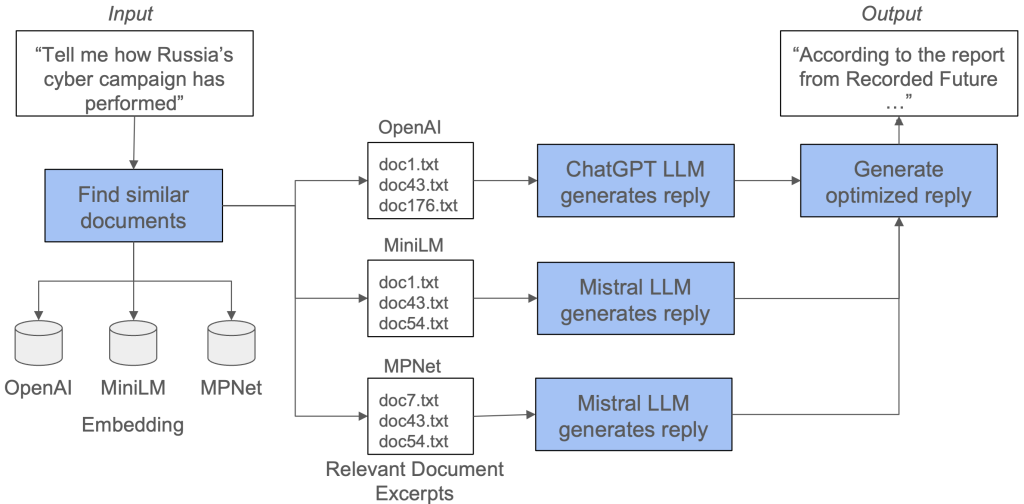
The Figure demonstrates the advanced LLM-RAG pipeline used by Last Heat Technologies to revolutionize intelligence gathering for our clients. Integrating three AI models, each contributing unique insights, our system efficiently filters and synthesizes large-scale data into coherent, mission-critical intelligence reports. This approach enables fast, precise analysis in dynamic environments. Looking ahead, Last Heat Technologies is paving the way for next-generation, self-aware systems that can autonomously refine their responses and adapt report generation to evolving data landscapes. These innovations are set to further empower our clients with intelligence solutions that are not only rapid but intuitively adaptive to new information.
Contact us
Last Heat Technologies
Buffalo, NY 14222
justin.delvecchio@lastheattechnologies.com
Drop us a line